

goharddrive
yeah i remember looking at some that had 5 year warrenty but they quickly sold out, and i was itching to build a ZFS pool as i waited for months to finally pull the trigger
Linux hobbyist, Machinist and tinkerer
Public Key 405B46E81DCCDB2B310DEF0DA5F0B998E8AC3752


goharddrive
yeah i remember looking at some that had 5 year warrenty but they quickly sold out, and i was itching to build a ZFS pool as i waited for months to finally pull the trigger


Amen brother!


i figured it out i had dns in the client wiregaurd config


Grammer is for english class or grammer community’s. Who cares


Yeah is guide is pretty useful! i went with setting up wireguard instead of openvpn. For a while now ive been self hosting alot of my stuff, SearXNG with gluetun tunneling, minecraft server for me and the boys and a Samba Share instead of paying for some dopey cloud storage. Ive gotten ZFS running in a 1tb z1 pool for my containers and plan to add a 10tb Z2 pool for long term storage and backups. i chose to do it in NixOS instead of debian or ubuntu, just because im a little bit of a nut for immutability.
its actually kinda funny i just left a post asking for help setting up wiregaurd server on c/selfhosted and referenced louis’s guide! Also i gotta add thats EPIC you got 10gbps internet, i went with a glinet flint 2 for my router. Because it runs openwrt under the hood, i personally like openwrt alot. there are people that swear by pfsense or opensense because of the bsd network stack, is very well maintained and secure as alot of commercial products like switches and firewalls run pfsense under the hood. for security and vlans pfsense would probably be better from what i heard. But openwrt works pretty well aswell, and i ended up just going with the flint 2 because it has 2.5gb wan in and 1 2.5gb lan. which was more than enough more my measly 1-2gb internet.


so for example, setting 192.168.8.170 on the clients as the only allowed IP aswell as the server would do what i need? thanks for helping trying to navigate my labyrinth of networking :P
For client example [Interface] Address = 10.0.0.3/24 ListenPort = 51820 PrivateKey = magic numbers
[Peer] PublicKey = magic numbers
PresharedKey = magic numbers
AllowedIPs = 192.168.8.170 Endpoint = magic numbers"
For server example
peers = [
{ #friend1 publicKey = “magic numbers and letters”; allowedIPs = [ “192.168.8.170/24” ]; endpoint = “magic numbers and letters”; presharedKey = “magic numbers and letters”; persistentKeepalive = 25; }
{ # My phone publicKey = “magic numbers and letters”; allowedIPs = [ “192.168.8.170/24” ]; endpoint = “magic numbers and letters”; presharedKey = “magic numbers and letters”; persistentKeepalive = 25; }
{# friend 2 publicKey = “magic numbers and letters”; allowedIPs = [ “192.168.8.170/24” ]; endpoint = “magic numbers and letters”; presharedKey = “magic numbers and letters”; persistentKeepalive = 25;
} {# friend 3 publicKey = “magic numbers and letters”; allowedIPs = [ “192.168.8.170/24” ]; endpoint = “magic numbers and letters”; presharedKey = “magic numbers and letters”; persistentKeepalive = 25; }


neat web app! the drawings kinda suck tho, but thats just a skill issue on my part :P


so if i understand this correctly, it runs a docker container to which runs the wireguard server and then you just specify hostname/ip adress for the services, then when sombody tunnels in they have acess to only the services specifide in config file? if so looks pretty useful!, i just question what happens to the rest of the traffic? is it locally routed in my network or client side? im not very familiar with proxys, i know what they are but have never really messed with one. Thanks for sharing


ok ill try to explain to the best of my ability and simply it.
i no longer want to use tailscale, because of accounts. i used to use tailscale for the minecraft server i want my friends to be able to acess only 192.168.8.170 on my local network and all other traffic to not be routed through my vpn but my friends to have acess to there internet on there LAN. example, we can play minecraft on the server on my network and we can be in a group call in signal. meaning friend 1 and 2 are using there internet connection locally, and only 192.168.8.170 being routed.
We also had some connectivity issues with tailscale, where friend 1 would be on and friend 2 would lag out of the server randomly. when if we played a game through steam we wouldnt have any connection issues. my friend is also very forgetful and cant log into his tailscale account, which is another reason why i wanna ditch tailscale.


so my friends wiregaurd config is
"[Interface] Address = 10.0.0.3/24 ListenPort = 51820 PrivateKey = magic numbers
[Peer] PublicKey = magic numbers PresharedKey = magic numbers AllowedIPs = 0.0.0.0/0, ::/0 Endpoint = magic numbers"
So if i understand the article correctly, i need to change it to
"[Interface] Address = 10.0.0.3/24 ListenPort = 51820 PrivateKey = magic numbers
[Peer] PublicKey = magic numbers
PresharedKey = magic numbers
AllowedIPs = 0.0.0.0/0, ::/0 Endpoint = magic numbers" Split tunneling: Exclude certain traffic from the VPN
PostUp = ip rule add from 192.168.50.0/24 table main
PostDown = ip rule delete from 192.168.50.0/24 table main
my friends LAN is 192.168.50.0/0 so im assuming were just trying to tell wireguard that anything within my friends subnet doesnt get routed? which means he will still be able to reach HigherGround@'192.168.8.170? and all of his other traffic will be local to him and go through his router?
im confused what “table” and “main” are im assuming its apart of iptables rules? im pretty new to IP tables so forgive me for my lack of understanding. i know its basically a linux purest firewall LMAO,
Then on my server i would edit
postUp = ''
${pkgs.iptables}/bin/iptables -A FORWARD -i cavein0 -j ACCEPT
${pkgs.iptables}/bin/iptables -t nat -A POSTROUTING -o enp5s0 -j MASQUERADE
'';
# Undo the above
preDown = ''
${pkgs.iptables}/bin/iptables -D FORWARD -i cavein0 -j ACCEPT
${pkgs.iptables}/bin/iptables -t nat -D POSTROUTING -o enp5s0 -j MASQUERADE
'';
And make it like this?
postUp = ''
${pkgs.iptables}/bin/iptables -A FORWARD -i cavein0 -j ACCEPT
${pkgs.iptables}/bin/iptables -t nat -A POSTROUTING -o enp5s0 -j MASQUERADE
${pkgs.busybox/bin/ip rule add from 192.168.50.0/24 table main
'';
# Undo the above
preDown = ''
ip rule add from 192.168.1.0/24 table main
${pkgs.iptables}/bin/iptables -D FORWARD -i cavein0 -j ACCEPT
${pkgs.iptables}/bin/iptables -t nat -D POSTROUTING -o enp5s0 -j MASQUERADE
${pkgs.busybox/bin/ip rule delete from 192.168.50.0/24 table main
'';
Right? or is step 4 on the client still? its not very clear in the article thanks for helping out!


 gronk use ms paint to describe.
gronk bad at explaining so he draws pretty pictures :P
gronk use ms paint to describe.
gronk bad at explaining so he draws pretty pictures :P
Thanks for the great memes! And contributing to the Fediverse


its flat theme


i think i may go with wire guard, do you know of any good videos or tutorials? i found this, https://www.digitalocean.com/community/tutorials/how-to-set-up-wireguard-on-ubuntu-20-04


also follow up question, alot of people are saying to make the mine-craft server run in a vm for host isolation. So what if i spun up 2vm’s
#1 would be a virtualized instance of pf sense, i would then have ethernet 1 on dogtown give internet to the base gentoo install, then have a Ethernet 2 go into PF sense, which will then have firewall rules to restrict access to the vm minecraft server. would that work? or is there somthing im misisng?
Diagram added
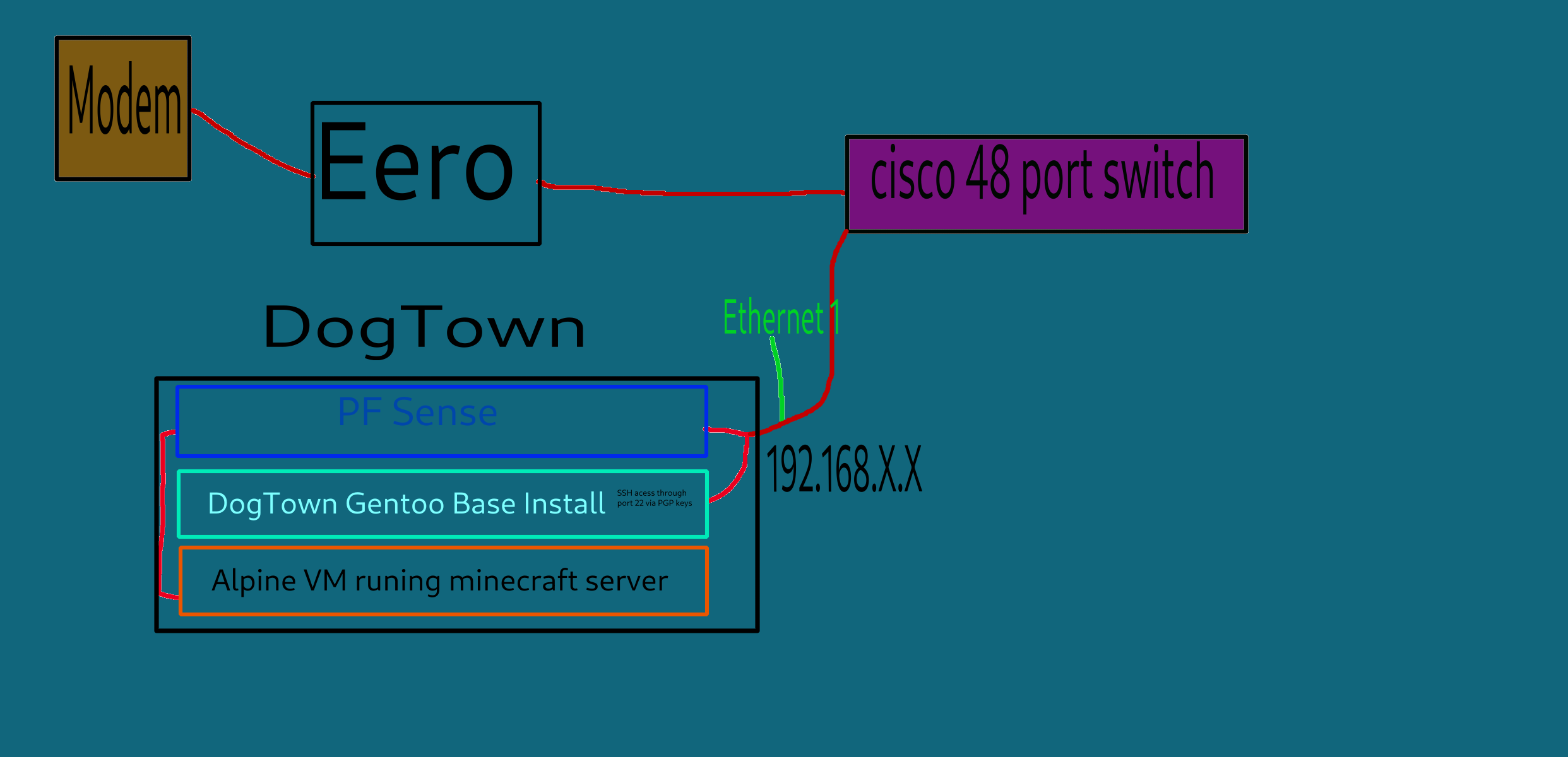


currently my setup is a dsl modem that goes, to my router/WAP which is a eero, that i plan to eventually replace with a Banna pi R4 which will run openwrt. but as of now the eero goes to my 48 port in my server room, and i have all my computer jacked into that. so to answer your question, my firewall is handled by my router and individual local rules by my machines. im kinda new to self hosting and port forwarding and pfsense looks pretty useful. i know pfsense is based on freebsd so is that a big plus vs openwrt?
please let me know, what some potential solutions could be.


Currently the plan is to use my 48 port cisco switch and put the server on a separate vlan. I assume that is very similar to your pfsense solution? Please correct me if im wrong


Damnn all for free! Lucky bastard
Lmao Put her to good use!


I got mediacom for my isp, My speed is about 1gb up and down Aswell We do not get phone or tv through our isp.
My house is old as balls and doesnt have ethernet or coaxial, i ran a ethernet cable up stairs for my rig.
And devices is around 13ish between people and my small fleet of raspi’s lmao
Do you like star trek and linux?